GL.iNet is a leading manufacturer for WiFi routers with openWRT pre-installed. It means that out of the box GL.iNet routers run openWRT. BlueMark Zero firmware is our solution to detect WiFi and Bluetooth BLE devices and runs on openWRT devices. It also means that BlueMark Zero is supported by these devices out of the box. With a few steps you can turn your GL.iNet device(*) into a device that detect WiFi and/or Bluetooth devices. BlueMark Zero supports the full range of GL.iNet routers.
(*) We support all openWRT devices that have a WiFi driver with a so-called monitor mode. If you are unsure if you device is supported, please contact us.
Install BlueMark Zero
Installing BlueMark Zero is easy.
 Setup your GL.iNet device (set up password, timezone)
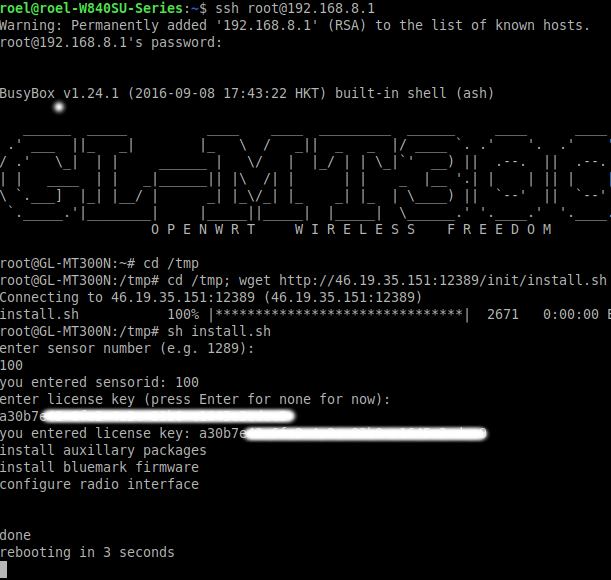
Setup your GL.iNet device (set up password, timezone)- Login to the GL.iNet device by SSH (e.g. ssh root@192.168.8.1)
- Retrieve the installation scrip and execute itt, enter this commands.
- cd /tmp; wget http://download.bluemark.io:12389/init/install.sh
- sh install.sh
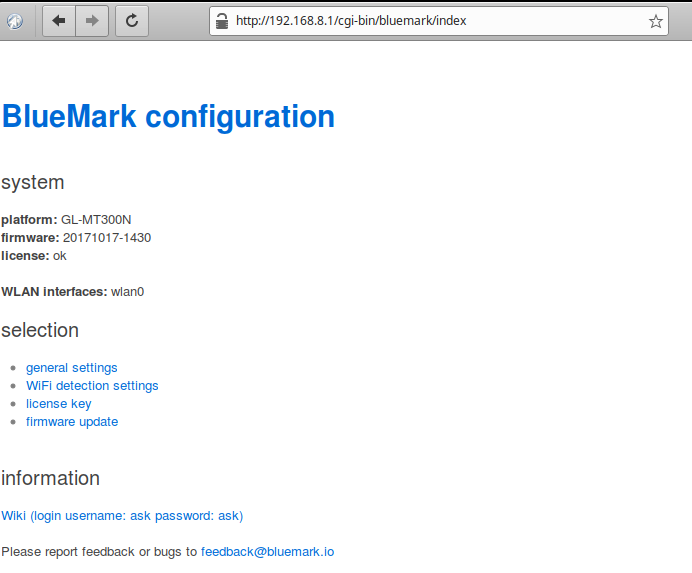
- The installation script will ask two questions, enter a sensor ID and a software license. The sensorID is a number to identify the sensor. For instance if you enter 100, all collected data will be assigned to sensor with sensorID 100. It is wise to choose sensor IDs unique. So you won’t have project with the same sensor IDs. The other questions is to enter a software license. This license is needed to unlock the firmware. Once installed the firmware will check roughly every 4 hours if the license is valid and if successful will unlock the firmware. Licenses can be generated at our license portal.
- After (automatic) rebooting your GL.iNet router will start sensing!
- Check the BlueMark detection settings at http://192.168.8.1/cgi-bin/bluemark/index (The regular URL http://192.168.8.1/bluemark does not work due to the GL.iNet firmware.)
- The BlueMark firmware supports different ways of outputting data. The firmware can act as TCP server and output the data as JSON or XML objects. The default output mode is to write the detected devices to SQL text strings. Periodically those files are compressed and sent to the server via SCP communication. To set this mode up, a SSH key has to be generated at the sensor. Its public key is needed at the server to authorise uploads
- By default the sensor has a demo SSH key installed, it allows to upload data to our demo server.
- At the sensor perform this command to generate a unique key: dropbearkey -t rsa -i /root/.ssh/id_rsa
- Use the public key at the server to allow the sensor to upload data. It is advised to use one key per project for security reasons.
- For more information please visit our wiki. (Ask our team for a login code.)